Last updated on December 12, 2022

What is Business Email Compromise (BEC)?
In BEC, an attacker gets access to a business email account and tries to copy the owner’s identity. This is done to trick the company, employees, customers or partners. Even technology giants have fallen due to these types of serious threats and attacks. This is also known as “man in the email attack”.
How is BEC carried out?
Source of the Image: https://www.fbi.gov/how-we-can-help-you/safety-resources/scams-and-safety/common-scams-and-crimes/business-email-compromise
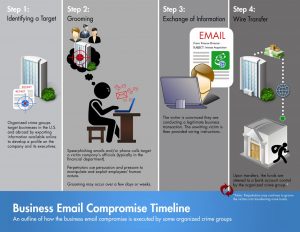
Phase 1 – Research and Identify targets
BEC attackers search contact data from websites, social media and the dark web. Then they make a profile of the targeted organization and its employees. These attacks usually focus on executives or employees of an organization who have the authority to make payments.
Phase 2 – Set up the attack
BEC attackers try to show that they are trustworthy. They try to win trust by spoofing email addresses, creating domains which look alike, impersonating trusted vendors and taking over email address of victim’s manager or colleagues.
Phase 3 – Execute the attack
An attack can be executed in one email or an email thread and in here the victim is persuaded by stating its urgent or showing authority. Then the perpetrator gives wire instructions to the victim and makes the victim do a payment to a fraudulent account.
Phase 4 – Disperse payments
When money is wired to the attacker, it’s collected fast and circulated among multiple accounts to reduce the ability of tracing. If the company is slow in identifying a BEC attack which has been executed in a successful manner, the chance of money being recovered is very less.
How to protect your company from BEC?
- Enable Multi-Factor Authentication (MFA) on accounts and workflows.
- Understand what your built-in email security can and cannot do, and make a plan to enhance baseline capabilities with security layers that can stop BEC attacks.
- Train employees to look for signs to identify Business Email Compromise attacks and also ask them to be skeptical when reading emails.
References:
https://cyberprotection-magazine.com/is-that-really-you
https://www.barracuda.com/glossary/business-email-compromise
https://www.armorblox.com/learn/business-email-compromise/

